MongoDB: How to read encrypted data from shell & what’s new with MongoDB 6.0 ?
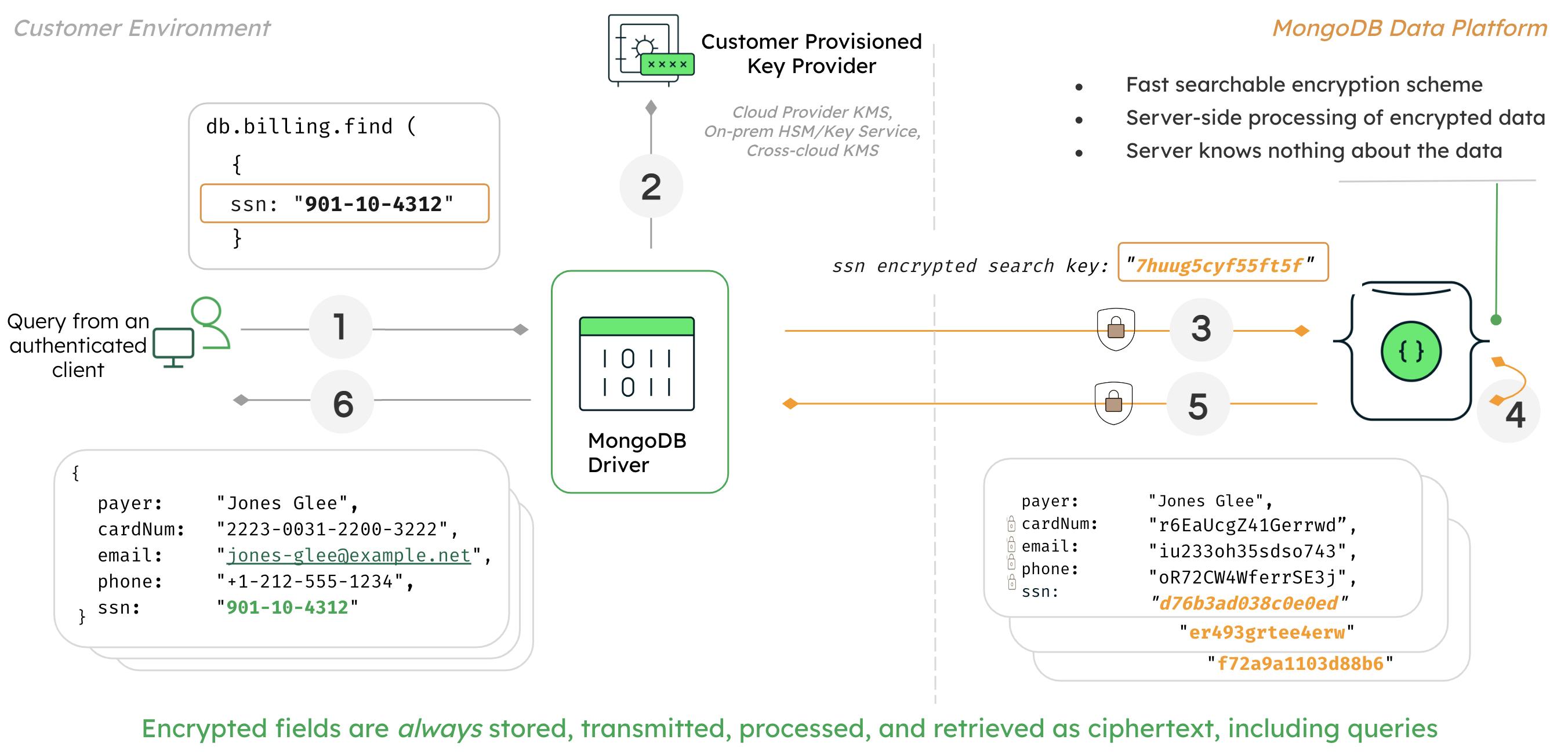
With MongoDB 6.0 introducing Queryable Encryption, MongoDB is the only database provider that allows customers to run expressive queries, such as equality (available now in preview) and range, prefix, suffix, substring, and more (coming soon) on fully randomized encrypted data. This is a huge advantage for organizations that need to run expressive queries while also confidently securing their data.
More Deatails at : MongoDB Releases Queryable Encryption Preview
Now let’s see how to simulate reading data from encrypted columns by passing the required keys to it.
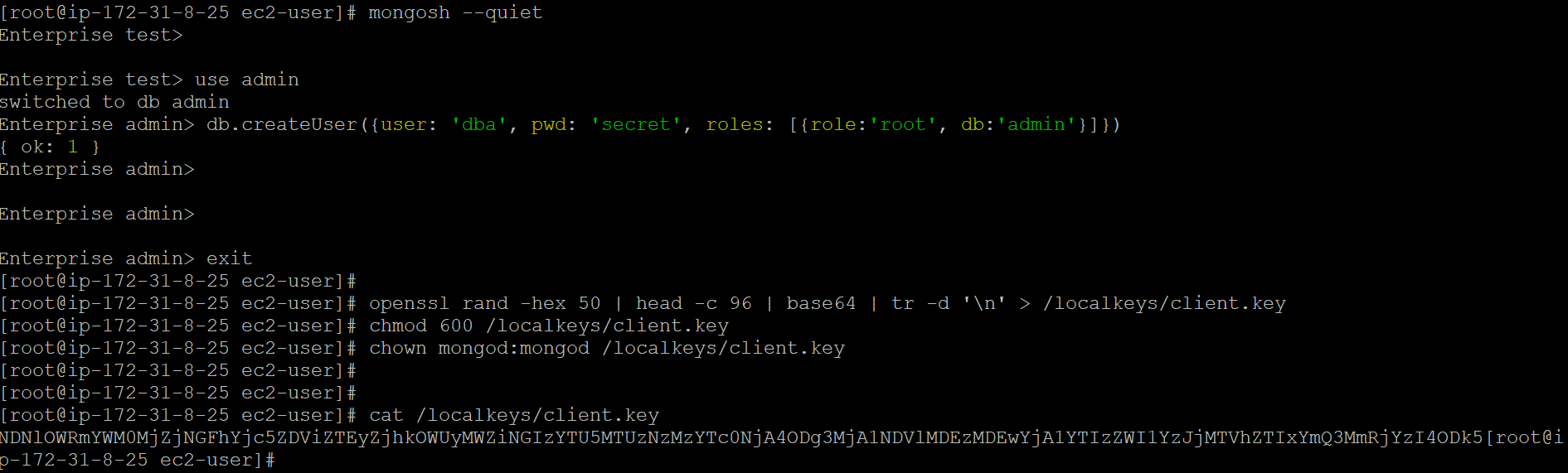
As a first step, enabled authentication and created locally managed KeyFile as below.
db.createUser({user: 'dba', pwd: 'secret', roles: [{role:'root', db:'admin'}]})
openssl rand -hex 50 | head -c 96 | base64 | tr -d '\n' > /localkeys/client.key
chmod 600 /localkeys/client.key
chown mongod:mongod /localkeys/client.key
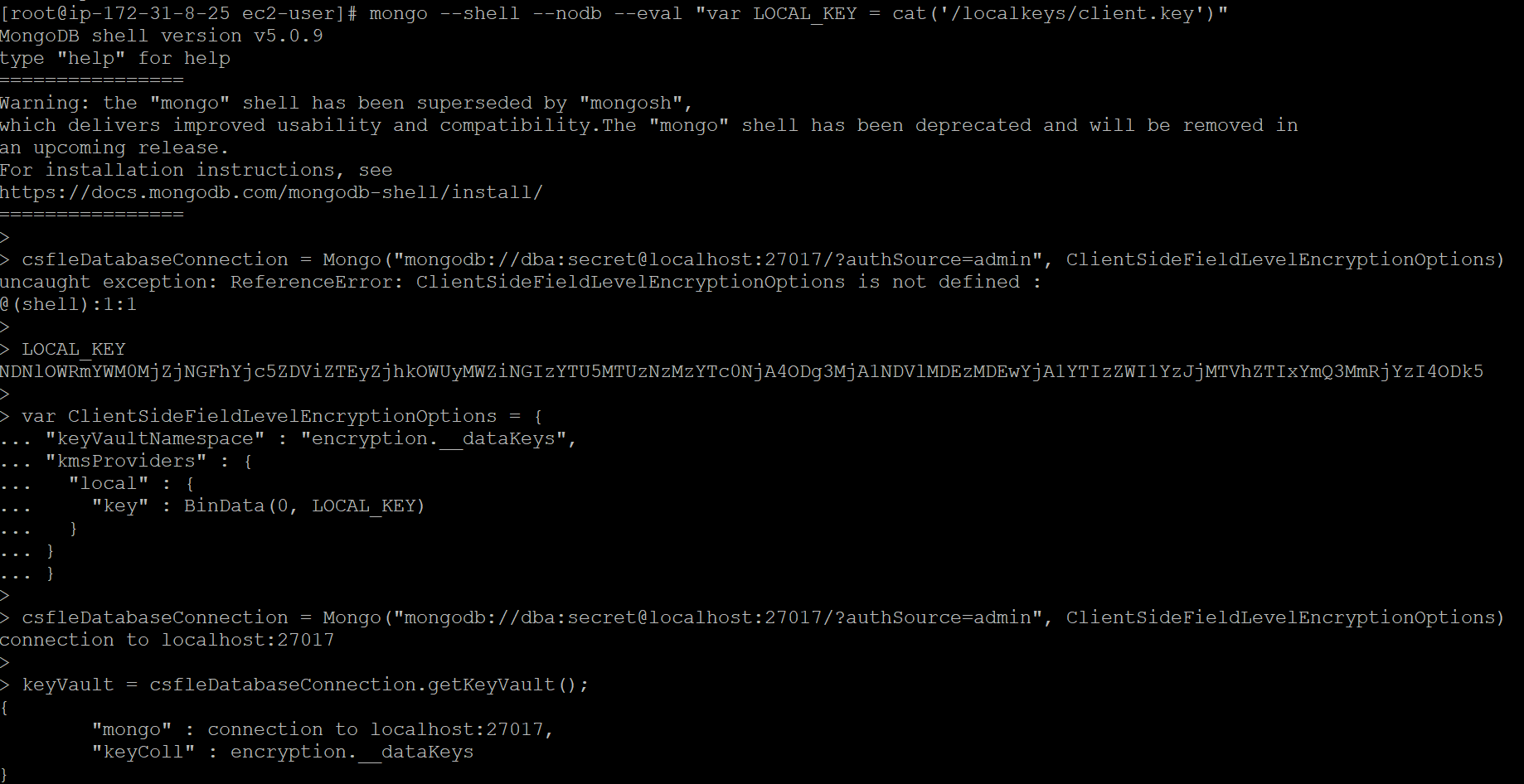
Loading the key into an object which will become a database connection, in the following example, we are loading our key file into the database variable LOCAL_KEY:
mongo --shell --nodb --eval "var LOCAL_KEY = cat('/localkeys/client.key')"
LOCAL_KEY
var ClientSideFieldLevelEncryptionOptions = {
"keyVaultNamespace" : "encryption.__dataKeys",
"kmsProviders" : {
"local" : {
"key" : BinData(0, LOCAL_KEY)
}
}
}
csfleDatabaseConnection = Mongo("mongodb://dba:secret@localhost:27017/?authSource=admin", ClientSideFieldLevelEncryptionOptions)
keyVault = csfleDatabaseConnection.getKeyVault();
Loading the document ClientSideFieldLevelEncryptionOptions using the proper client-side field-level encryption configuration:
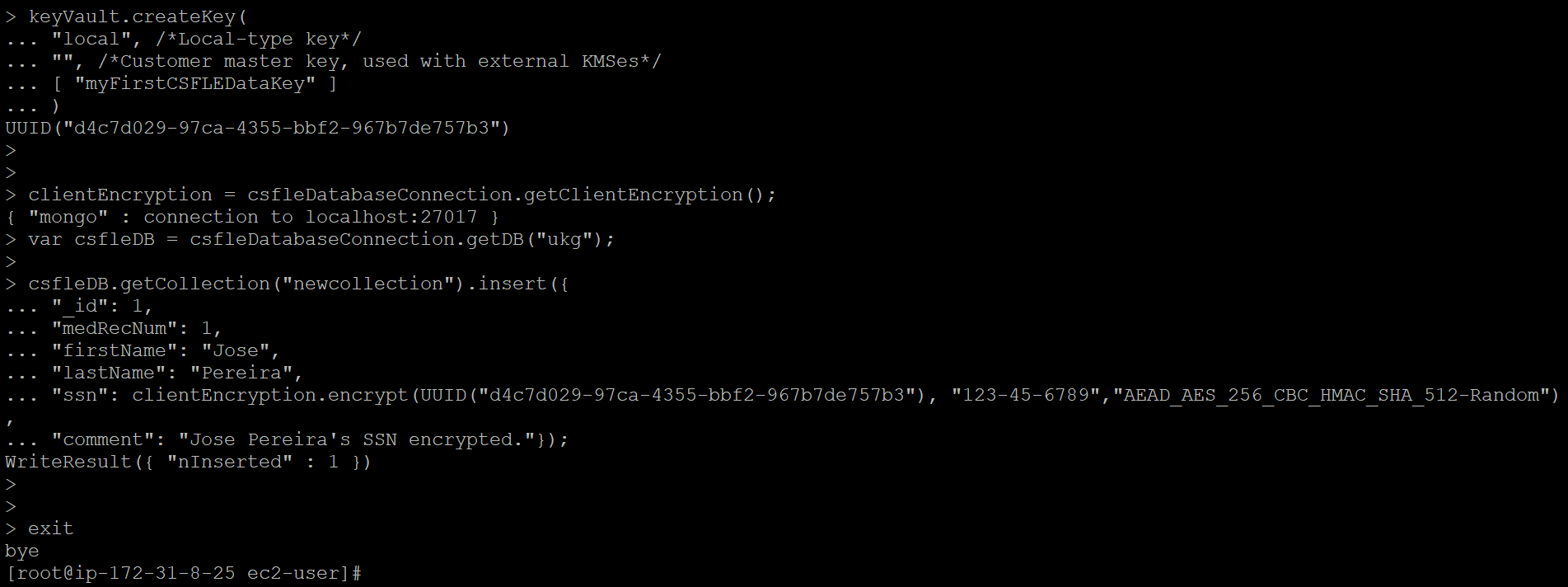
keyVault.createKey(
"local", /*Local-type key*/
"", /*Customer master key, used with external KMSes*/
[ "myFirstCSFLEDataKey" ]
)
clientEncryption = csfleDatabaseConnection.getClientEncryption();
var csfleDB = csfleDatabaseConnection.getDB("ukg");
csfleDB.getCollection("newcollection").insert({
"_id": 1,
"medRecNum": 1,
"firstName": "Jose",
"lastName": "Pereira",
"ssn": clientEncryption.encrypt(UUID("d4c7d029-97ca-4355-bbf2-967b7de757b3"), "123-45-6789","AEAD_AES_256_CBC_HMAC_SHA_512-Random"),
"comment": "Jose Pereira's SSN encrypted."});
fter setting the variable; We can establish an FLE-enabled connection using the above variables via ClientSideFieldLevelEncryptionOptions on Mongo() constructor.
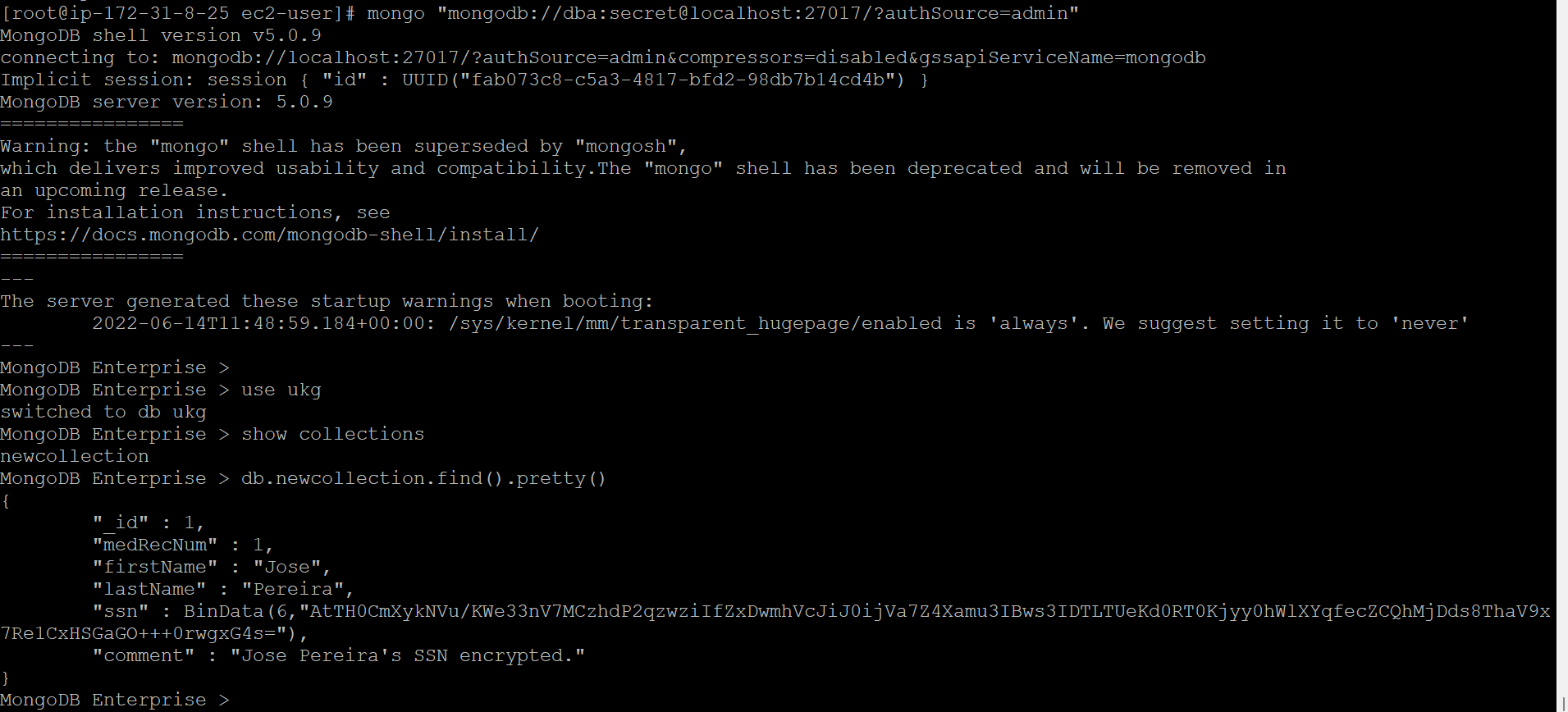
mongo "mongodb://dba:secret@localhost:27017/?authSource=admin"
use ukg
show collections
db.newcollection.find().pretty()
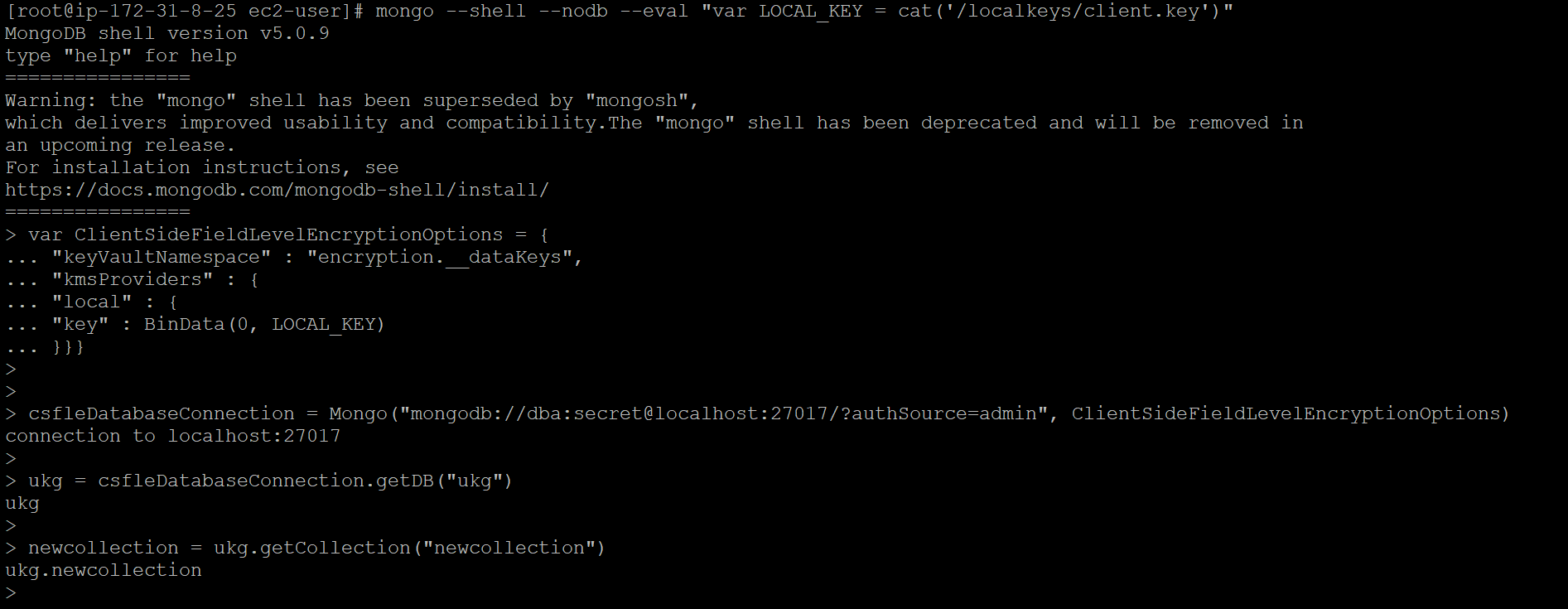
To read, the client must load the ClientSideFieldLevelEncryptionOptions configuration into its session; By opening a connection, load the options into the variable, and use the Mongo() constructor to logging without the requirement of key vault configuration:
mongo --shell --nodb --eval "var LOCAL_KEY = cat('/localkeys/client.key')"
var ClientSideFieldLevelEncryptionOptions = {
"keyVaultNamespace" : "encryption.__dataKeys",
"kmsProviders" : {
"local" : {
"key" : BinData(0, LOCAL_KEY)
}}}
csfleDatabaseConnection = Mongo("mongodb://dba:secret@localhost:27017/?authSource=admin", ClientSideFieldLevelEncryptionOptions)
ukg = csfleDatabaseConnection.getDB("ukg")
newcollection = ukg.getCollection("newcollection")
ukg.newcollection.find().pretty()
Reading an Encrypted Field :


Comments are closed, but trackbacks and pingbacks are open.